Ensure your DR strategy meets the challenges of a new decade
Traditional disasters and new cyberthreats have organizations reexamining their DR plans to ensure they maintain high levels of availability and can restore operations quickly.
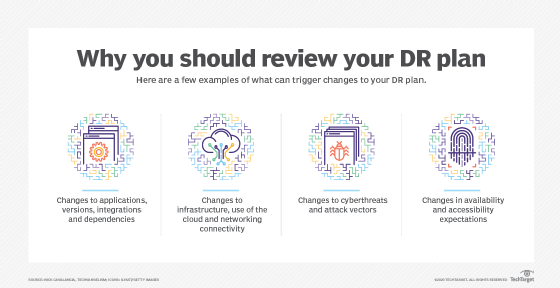
If your organization is serious about disaster recovery, you understand the importance of having a DR strategy that reflects the current state of the business. Changes in applications, business functions and workloads and shifts from on-premises to the cloud require a review of and update to your DR plan.
Shifts in the recovery time and recovery point expectations put upon your business by customers, employees, contractors, supply chains and partners can also mandate a review. For example, last year's plan to get back up and running in one hour after a disaster may no longer be fast enough to avoid a financially negative impact to the business.
Additionally, cyberattacks are becoming more frequent and sophisticated in nature. The bad guys now realize it's far more profitable to dig around your network, gain an understanding of the business and look for multiple ways to make money off your organization through fraud, data theft, holding data ransom or simply selling access to your network.
As a new decade begins, it's time to examine your DR strategy in light of these updated availability concerns and threats. This article will cover what parts of your DR plan need to be evaluated, as well as why and how to better use recovery plans to ensure higher levels of availability.
What's new in the world of disasters?
If you have an IT DR plan, you're familiar with the traditional list of disasters -- hurricanes, floods, power outages and fires -- you need to recover from. But what else do you need to consider as a potential disaster? This year's list should include several types of cybersecurity-related disasters with thought paid to the specifics of each one to ensure you can recover from them correctly.
Unless you've been hiding under a rock, you know the threat of ransomware exists. Let's dig into a few particular ransomware attack methods that may change the way you respond to ransomware as a disaster:
- Backups are a target. Today's ransomware is no longer just about encrypting files. In addition to critical business data, both backup filetypes and even NAS storage devices -- presumably because they are likely to house on-premises backups -- are now ransomware targets. You should consider storing backups in the cloud so they are safe from on-premises ransomware attacks.
- Every system is the goal. Cybercriminals realize the value of bringing your operation to its knees, so newer strains of ransomware focus on maximizing the number of systems that can be connected to and encrypted. This affects how many systems you may want to back up to ensure not just recoverability, but productivity.
- Attackers are becoming more patient. Rather than infect and immediately encrypt, cybercriminals are programming ransomware to lie in wait, sometimes for as long as a few months, to ensure plenty of backups of the infected system have been created. This is done so when encryption does occur, recovering to a clean backup is nearly impossible, increasing the probability of a payout of the ransom. This may require using backup integrations that scan backups as they are created or before they are recovered.
When a cybercriminal successfully steals data, you might think there's no recovery to be done. Nothing could be further from the truth. There are a number of tactics used during data breaches that can affect your DR strategy:
- Lateral movement is implemented. According to Carbon Black's "2019 Global Threat Report," 60% of cyberattacks involve lateral movement -- the use of internal and usually elevated credentials to move from system to system within an environment. In many cases, these attacks replace Windows service executables, change system permissions and even modify group policies in Active Directory (AD).
- Persistence is established. Cybercriminals look for ways to maintain their ability to get back into your environment. By gaining some level of administrative access to AD, usually as a function of looking for privileged credentials during lateral movement, they create multiple user accounts. If one fake account is found, there are plenty more they can use that you don't know about.
- Privileges are granted. Cyberattacks often modify group memberships to assist with persistence or grant access to resources. In many cases, groups are created and deeply nested to avoid detection.
In all of the above tactics, the result is that AD is no longer in a known-secure state after a data breach. You have no idea if extra accounts exist, what privileges have been granted or whether an attacker can still get in and do more damage. Should a data breach occur, you need to include recovering AD to a state prior to the breach as part of your updated DR strategy.
Where should you start your 2020 DR review?
Evaluate your plan using the same steps used to craft it. Start with a business impact analysis (BIA) and risk assessment, plug in these new disasters and then formulate an update to address any identified risks.
The high-level purpose of a BIA is to identify those operations the business can't do without, for example the lack of availability of a critical application. Questions to ask might include the following:
- What functions are relied upon daily?
- What amount of data loss is acceptable?
- What amount of operational loss is acceptable?
But what if a subset of the data the application relies upon is encrypted as part of a ransomware attack or manipulated as part of an insider threat? Data normally considered simply part of a critical application or workload may now need to be its own critical business function separate from the application.
Normally, DR planning remains at a business function level that doesn't necessarily consider the specific systems and data involved. But with these new types of ransomware attacks purposely going after backups and backup storage, it's prudent to consider separating business functions to some degree into the application that services the business function and the data that supports the application and then measuring the business impact.
The risk assessment should review the disasters you believe are probable and then match those against the business functions in the BIA to identify the scenarios you need to plan for. If the last version of the risk assessment doesn't include cyberincidents, add them, and consider how each of those attacks will technically alter your environment and result in a new recovery scenario to address.
You should walk away with some idea of the gaps that exist in your current recovery capabilities. This will help you implement updated DR strategies to minimize the disruptions outlined in the risk assessment.
Much of your underlying DR plan -- including its goals, defined roles, requirements and procedures -- won't change too much. But there are processes you might want to add, including some that will affect your data backup environment.
Because the business experiences its own evolution, you might have planned for changes that will happen over time. These are primarily modifications in recovery point objectives and recovery time objectives that require more frequent backups, the use of replication or even a shift to using cloud infrastructure to ensure desired levels of availability.
You may also need to supplement the normal "we need to include the ability to recover AD or permissions" part of your DR strategy with something that may seem a bit out of place: a security team that identifies systems that have possibly been affected by a cyberincident.
For example, if your organization was the victim of a data breach and the security team determined the attacker compromised seven systems, created accounts in AD and granted themselves privileges to specific databases via group memberships, you need to know which systems need to be recovered and when the changes were made. This will enable you to recover everything to a state prior to the attack as the cyberattackers may have a remote access trojan installed to provide further external access. In some cases, you may need to perform object-level recovery to undo specific changes rather than a blanket reversion of AD to some earlier date.
Organizations serious about their DR strategy planning should also include testing, whether it be tabletop walkthroughs, recovery simulations or something in between. For each new recovery scenario you come up with, be certain you've identified DR plan testing to ensure the highest levels of success.
Recovering Active Directory may be problematic
Recovering Active Directory will have repercussions of its own. It's not wise to make assumptions about which parts were touched by an attacker, so you may have to recover all of AD to remediate any risk.
You'll likely have Windows endpoints that may need to be rejoined to the domain because computer accounts have reverted to earlier versions, and there may be users with old passwords that may need to be reset and -- potentially -- applications and services that use AD accounts that need to be updated.
Including a security team in your DR plan enables organizations to better understand what needs to be recovered and back to when. If it's possible to simply revert a few accounts to previous versions, you would avoid the ripple effect caused by an AD recovery.
Looking back to prepare ahead
The start of a new year is when people reflect on what's occurred thus far in their lives and consider changes that may provide a better outcome. It's no different for organizations. It's quite possible your DR strategy has gone stale and no longer reflects the current state of threats and resulting action plans.
By reviewing your DR plans for their readiness against any and all threats to business availability, you materially improve your organization's chances of restoring operations quickly. Don't cut corners. The success of your review depends on how thoroughly you look at your DR strategy from start to finish. And given the potential impact some of these new cyberattacks can have on a business, it's critical to ensure you have a proper response in place.







