IT risk assessment template (with free download)
Risk assessments are a critical part of a disaster recovery plan. Find out how to prepare a risk assessment, then download our included free template to create one.
Risk assessments and business impact analyses are crucial resources in a disaster recovery plan.
While the two processes might sound similar on the surface, they each serve a different critical function. While a BIA helps identify an organization's most critical business processes and describes the potential impact of a disruption to those processes, a risk assessment identifies the internal and external situations that could negatively affect the critical processes. A risk assessment weighs the likelihood of any given crisis an organization might face.
Below, find out how to prepare a risk assessment and how to identify and respond to natural and human-made hazards. Organizations can then customize the included free, downloadable IT risk assessment template to aid their disaster recovery (DR) plan.
Why are risk assessments important?
DR is an expensive practice, and risk assessments can help keep costs down. Risk assessments prepare organizations for the most likely threats, enabling them to shift resources to the risks most likely to strike and avoid unnecessary expenses.
A risk assessment helps identify events that could adversely affect an organization. This includes potential damage events could cause, the amount of time an organization will need to recover or restore operations, and preventive measures or controls the company can take to mitigate the likelihood of an event occurring. A risk assessment will also help determine what steps, if properly implemented, could reduce the severity of an event.
How to conduct a risk assessment
To get started with a risk assessment, begin by identifying the most critical business processes from the BIA. You should then gather information on potential threats to your organization.
There are numerous sources available to help you gather threat information, such as the following:
- Company records of disruptive events.
- Employee recollection of disruptive events.
- Local and national media records.
- Local libraries.
- First responder organizations.
- National Weather Service historical data.
- U.S. Geological Survey (USGS) maps and other documentation.
- Experience of key stakeholder organizations.
- Experience of vendors doing business with the firm.
- Government agencies, such as the Federal Emergency Management Agency, Department of Homeland Security and Department of Energy.
These sources can help determine the likelihood of specific events occurring, as well as the severity of actual events. You can rule out certain events if there is almost no chance of them occurring. For example, you don't have to plan for earthquakes if USGS maps indicate your site is not in or near an earthquake zone. Use the included risk assessment template to list and analyze potential threats to your organization.
An excellent document to assist in preparing a risk assessment comes from the National Institute of Standards and Technology. The document is Special Publication 800-30 Rev. 1, Guide for Conducting Risk Assessments.
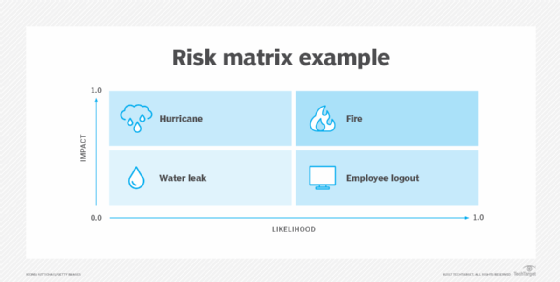
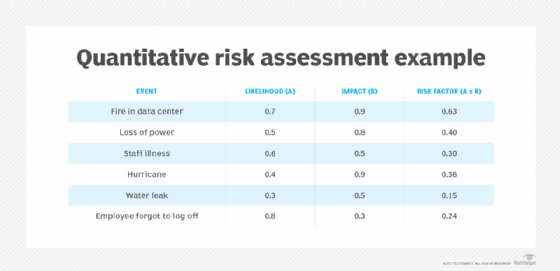
A basic formula, risk equals likelihood multiplied by impact, typically computes a risk value. This formula is also known as a risk assessment matrix. By weighing the likelihood of an event against the level of damage it could cause, the risk assessment matrix is an illustrative tool management can use to plan for possible disasters.
For example, use a scale of 0.0 to 1.0, in which 0.0 means the threat is not likely to occur and 1.0 means the threat will absolutely occur. The impact 0.0 means there is no damage or disruption to the organization, whereas 1.0 could mean the company is destroyed and unable to conduct business. Numbers in between can represent the result of a statistical analysis of threat data and company experience. The downloadable risk assessment template uses this approach.
With the quantitative range 0.0 to 1.0, DR teams might decide to assign qualitative terms to results -- e.g., 0.0 to 0.4 = low risk, 0.5 to 0.7 = moderate risk and 0.8 to 1.0 = high risk.
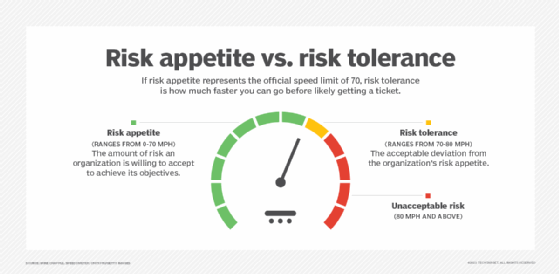
Once IT teams have analyzed relevant risks and assigned a qualitative category, they can examine strategies to deal with only the highest risks or address all the risk categories. The risk management plan will depend on management's risk appetite, which is their willingness to deal appropriately with risks. Risk appetite represents how much risk management is willing to accept, so responses will vary by organization. The strategies for risks can next be used by DR teams to help design business continuity and DR (BCDR) strategies.
Who conducts risk assessments?
Project managers and their teams are typically in charge of risk assessments and risk management plans. Personnel might be involved when it comes to actions that might need to be performed at that level in the future.
Once a risk assessment is done, BCDR teams use it to craft plans and run exercises to test DR plans. These teams might also indicate when the organization needs to update the risk assessment if the risks seem out of date during tests and planning exercises.
Threats and vulnerabilities
A risk analysis involves identifying a risk, assessing the likelihood of an event occurring and defining the severity of the event's consequences. It might also be useful to conduct a vulnerability assessment, which can help identify situations where the organization might be putting itself at increased risk by not performing certain activities. An example might be the increased risk of viruses by not using the most current antivirus software.
Finally, the risk analysis results should be summarized in a report to management, with recommended mitigation activities. It might be useful to look for vulnerabilities while performing a risk analysis.
The level of detail in a risk assessment will vary by organization, depending on the number of effects, symptoms and consequences. There is no set number of risks to look for in a general risk assessment, so that is up to the discretion of the company performing the assessment. In the included risk assessment template, there are fields for more than 50 potential hazards, both human-made and natural.
Types of risk assessments
Risk assessments generally take one of two forms: quantitative and qualitative.
Quantitative methods. These methods assign a numeric value to the risk and usually require access to reliable statistics to project the future likelihood of risk.
Qualitative methods. These often include subjective measures, such as low, medium and high. Qualitative methods are based on gaining a general impression about the risks to qualify them.
The risk assessment process can be relatively simple -- for example, if organizations elect to use a qualitative approach. They can be more rigorous when using a quantitative approach, as IT teams might want to substantiate numerical factors with statistical evidence.
How often organizations carry out a risk assessment is also up to their discretion. However, DR teams must update results periodically to determine if any changes to the risks have occurred. Regardless of the methodology, the results should map to the critical business processes identified by the BIA and help define strategies for responding to the identified risks. If a risk assessment is outdated, so are the strategies that will combat potential hazards.
Sometimes, the qualitative approach is more acceptable to management since a relative comparison can be easier to draw conclusions from than an objective number. In the included risk assessment template, there are columns that enable DR teams to assign qualitative terms to each of the risks to their organization.
4 types of defensive responses
After DR teams identify the risks and vulnerabilities, they can consider defensive responses. The sequence in which these measures are implemented depends, to a large extent, upon the results of the risk assessment, but the major defensive response types include the following:
- Protective measures. These activities reduce the chances of a disruptive event from occurring. One example is using security cameras to identify unauthorized visitors and alert authorities before an attacker can cause any damage.
- Mitigation measures. These activities minimize the severity of the event after it occurs. Mitigation measure examples include surge suppressors to reduce the effect of a lightning strike and uninterruptible power systems to limit the chances of a hard stop to critical systems due to a blackout or brownout.
- Recovery activities. These activities restore disrupted systems and infrastructure to a level that can support business operations. For example, critical data an organization stores off-site can restart business operations to an appropriate point in time.
- Contingency plans. These process-level documents describe what an organization can do in the aftermath of a disruptive event. They are usually triggered based on input from the emergency management team.
Types of hazards
Hazards are unique combinations of events and circumstances. The two primary categories are human-made and natural.
Human-made hazards are those in which an individual or multiple persons might be held accountable for contributing to the event(s) that caused a disaster. This could be through deliberate or accidental causes. These hazards might include malware attacks and accidental or malicious data deletion.
Natural hazards are typically considered incidents for which there is no one to blame, such as weather events like earthquakes and tornadoes. If an organization is in an area prone to hurricanes or if a building has construction vulnerabilities, DR teams should make note of that in a risk assessment.
Grouping impacts
After the organization has identified the risks, it will identify three major factors: the effects, symptoms and consequences of the event.
Effects
The following five basic effects can have disastrous consequences:
- Denial of access.
- Data loss.
- Loss of personnel.
- Loss of function.
- Lack of information.
Symptoms
The perceived symptoms might be a loss -- or lack -- of the following:
- Access or availability.
- Data.
- Confidentiality.
- Data integrity.
- Environment.
- Personnel (temporary loss).
- System function.
- Control.
- Communication.
Consequences
Secondary effects or consequences might include the following:
- Interrupted cash flow.
- Loss of image.
- Brand damage.
- Loss of market share.
- Lower employee morale.
- Increased staff turnover.
- High costs of repair.
- High costs of recovery.
- Penalty fees.
- Legal fees.
A risk assessment is a key activity in a BCDR program. Disruptive events can be unpredictable and unavoidable, but any preparation prior to a disaster will make BCDR more attainable. Risk assessments, BIAs, DR tests and resilience exercises are all critical components of a BCDR plan, and most organizations will find that they're worth the time and expense.
Paul Kirvan is an independent consultant, IT auditor, technical writer, editor and educator. He has more than 25 years of experience in business continuity, disaster recovery, security, enterprise risk management, telecom and IT auditing.






